I recently wrote a post about NZ’s COVID-19 contact tracing app. This companion article will look at the approaches taken by Australia, Singapore, the UK and Switzerland. The Swiss app is interesting because it’s the first to use Google and Apple’s anonymous contact tracing API ExposureNotification. The post will start by giving a brief intro to Bluetooth contact tracing, then comparing the privacy and security of the aforementioned implementations.
Bluetooth Contact Tracing: A Primer
Most COVID-19 tracking apps use Bluetooth to identify other devices (people) in close proximity. To give a simple explanation, apps both broadcast and listen for identifying data packets.

Later, if Alice is diagnosed with COVID-19, she can upload a list of all the other users she saw to the health authority in her country (or state, county, etc).

The health department then has a record of who has interacted with Alice and can identify and notify those contacts.
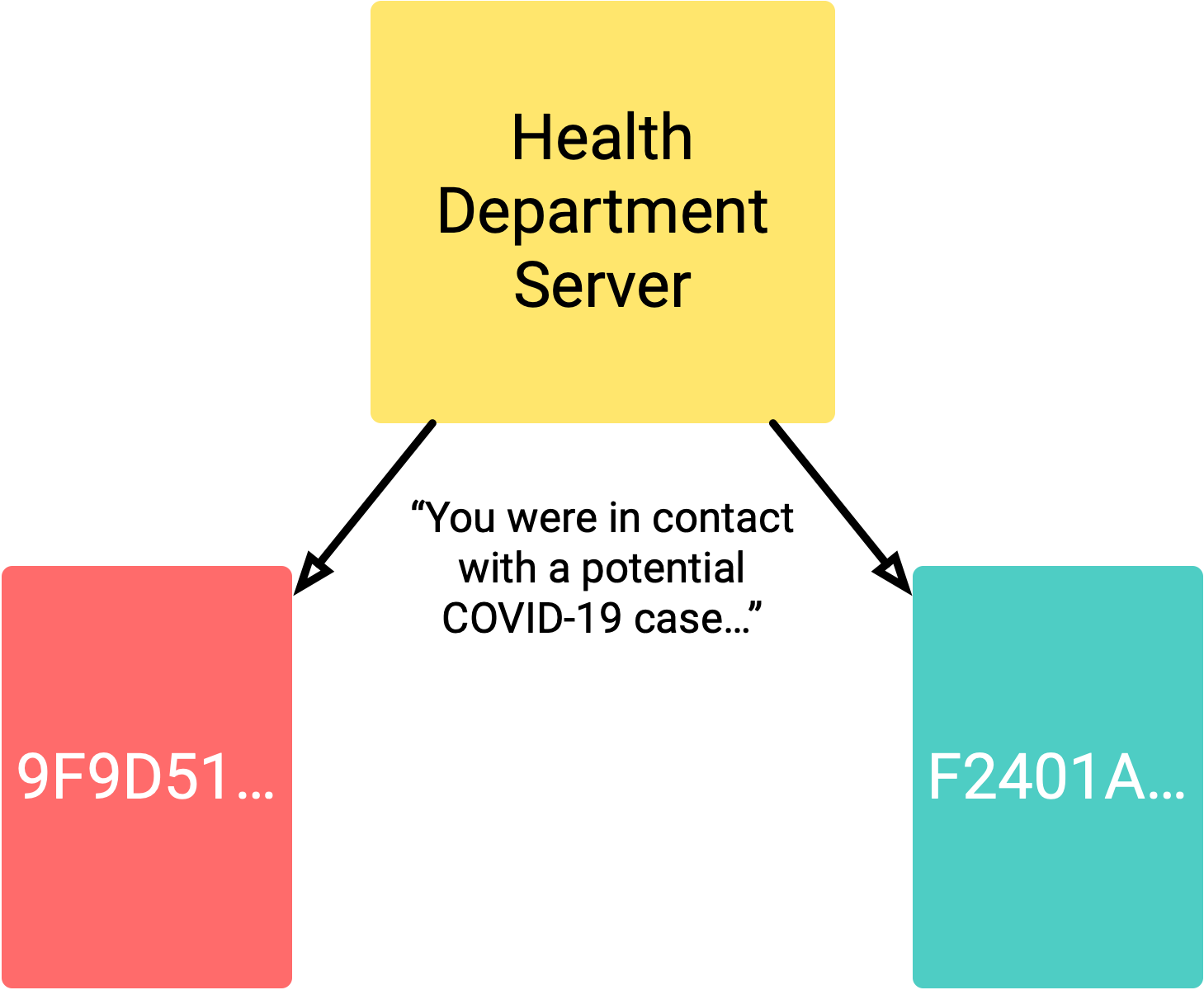
The data being transferred, and its uniqueness to a specific user, varies across the different apps/countries. This is something we’ll go into further detail later on. The general idea is that someone could know which IDs it has seen, but can’t then use those IDs to identify a particular person. An important consideration from both a general privacy and medical privacy standpoint (i.e. identifying if a particular person has COVID-19). In theory, this sounds simple. In practice, getting all this right can be difficult. As well as the privacy problems to solve, there are also technical limitations.
For example, apps running on iOS are limited in what they can do in the background. Instead of executing in perpetuity, apps in the background are awoken by the OS periodically and have a limited amount of time (10 seconds) to do what they need to do. This in turn limits how long an iOS device has to communicate with other contact devices.
iOS 13.5, released a few days ago, includes the Apple/Google ExposureNotification API. This runs at a lower level on the system and thus has support for more frequent polling. This is not an app in and of itself, instead it is just an API that apps must be built to take advantage of. Android apps have much fewer restrictions on what they are allowed to do in the background, and so are not as reliant on a new system API. Google’s version of ExposureNotification, however, is available for Android 6.0 (Marshmallow) or later.
Now that Bluetooth contact tracing is introduced, we’ll take a look at the implementation for a few countries.
Australia
The Australian contact-tracing app is COVIDSafe. It generates a new user ID every two hours. This rolling ID is encrypted with the Australian Department of Health’s public key before being transmitted using Bluetooth to nearby phones.
A brief intro to private/public key cryptography: keys are generated in pairs. Data can be encrypted with a public key but can only be decrypted with the corresponding private key. Therefore it is “safe”* to distribute the public key as part of the app, because the private key for decryption is being kept secure.
*The use of “safe” here implies that the private key is indeed being kept securely.

If you’re diagnosed with COVID-19, you can upload the list of all the devices you’ve seen to the Department of Health. They then decrypt the IDs and match them to the people you have been in proximity to, and then contact them. Therefore, while the DoH has information about which person has had a specific ID, it doesn’t have a record of proximity information unless the user has been diagnosed and consented to uploading the data.
This is all done by proximity to others and doesn’t require recording your location, which is good from a privacy standpoint. Since the ID is rolling, it also doesn’t allow a specific user’s movements to be tracked (at least not for more than two hours).
Singapore
Singapore’s app is TraceTogether. It functions very similarly to COVIDSafe.
Its privacy statement page doesn’t make it clear how often its transmitted ID changes, other than that it is “refreshed at regular intervals”. Also like the Australian approach, only the Singaporean Ministry of Health can decrypt the data with their private key. A particular user’s contact data is only uploaded to the MoH, and so no contact tracing record exists until the user has consented and uploaded.
The UK
The UK’s NHS COVID-19 App uses similar Bluetooth tracing techniques as Australia and Singapore. Unfortunately, it appears that it bucks the trend by generating a unique ID for each app install, rather than periodically rotating it.
Note that the information presented here is based on the NHS’ website, which may be omitting detail in order to be more understandable to a layperson.
No mention is made of encrypting the ID before transmission which leads me to believe that a single ID could be traced back to a person. Proximity information could then be determined by reading data off a single phone.
This “what-if” scenario depends on a number of breaches of personal phones being performed, as well as the NHS’s data. However, it would still be better with rolling IDs or some form of encryption.
Switzerland
The first app that has been released implementing Apple/Google’s ExposureNotification API is SwissCovid. This description of the apps behaviour will be based on the specification document of ExposureNotification itself, rather than the app.
The API generates a unique ID which changes about every 15 minutes. This is the data that is transmitted over Bluetooth. If someone tests positive for COVID-19, they can choose to upload their last 14 days (give or take) of IDs to a server.
Apple and Google do not operate these servers, they just provide implementation detail. Usually it will be a department of health or similar that runs such a server.
These are its own IDs, not those of who it’s seen.

Unlike the previous tracing implementations, the server does not notify close-contacts that they may be affected. Instead, the app will periodically download a list of infected IDs in the background. If your phone finds a match between this list and someone it has seen, then it will alert you.
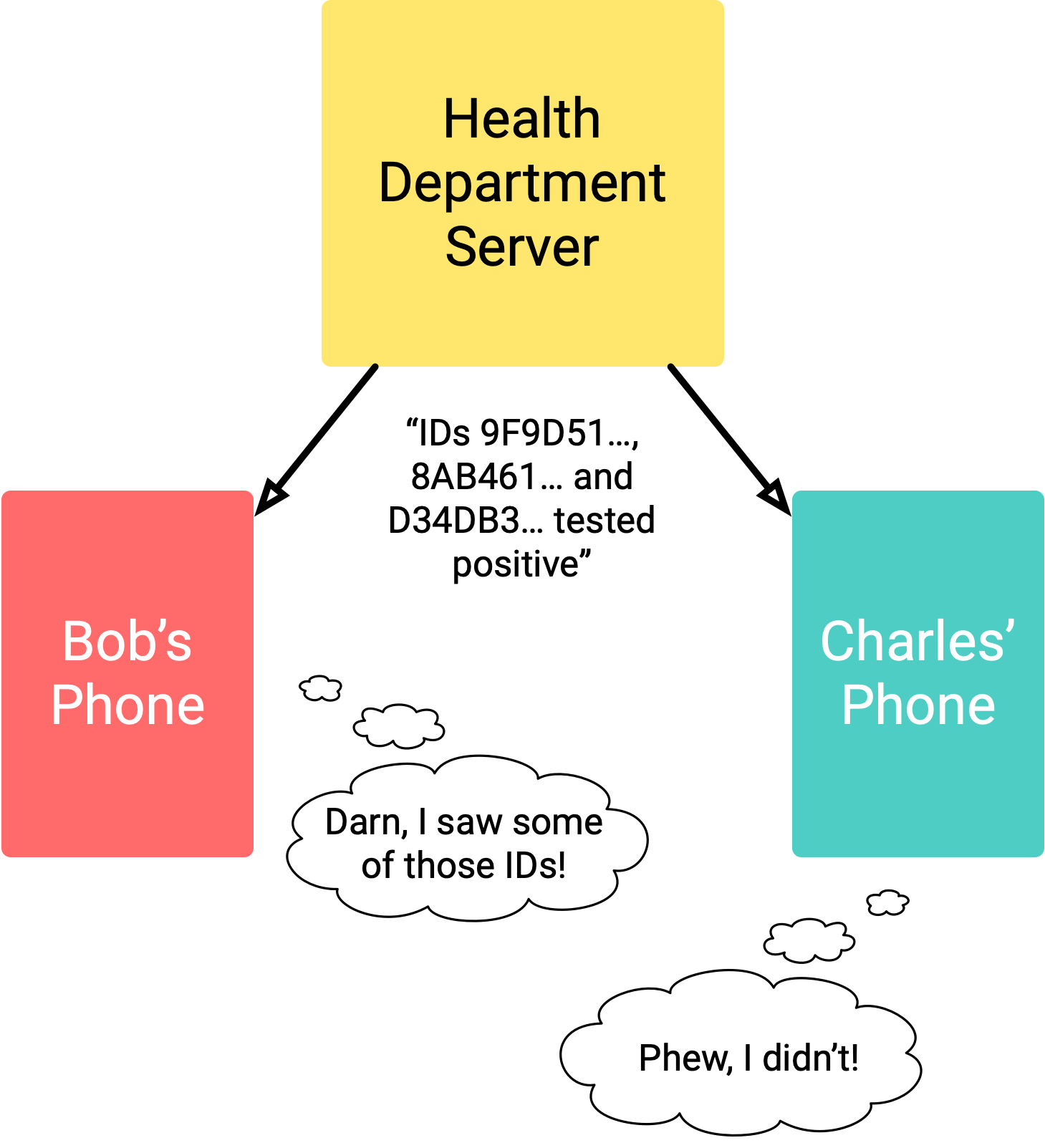
This way, contact tracing is completely anonymous and not even the government departments have information about who has been in contact with who. The server doesn’t even need to know who you are.
Conclusion
While the idea behind using Bluetooth to perform contract tracing sounds simple, the alternative implementations may have different impacts on how well they work. Only time will tell if these differences have any meaningful effects on virus tracing. It would be great to see, in the future, all tracing apps updated to use Google/Apple’s ExposureNotification. I believe this is the best anonymous tracing API, because it doesn’t share who you’ve been in contact with or even track your location. All that is reconciled on your device itself.
On a less technical note, it’s great to see that the apps I’ve looked at have great privacy policies with enough technical detail published to understand how they work. Australia and the UK have made their apps open source, which means anyone can verify that their behaviour matches the described implementation.